-
Hackers automate, so should you!
"Companies will continue to face the cold reality that throwing people at the problem is no longer sufficient for remediating vulnerabilities and combating the sheer volume of automated attacks,"
"They need solutions that are as automated as the attacks that continue to hammer them -- fixing vulnerabilities manually is no longer possible in the 'new normal."
Some of the benefits of our services.
At NETSyntropy, we know the lack of basic blocking and tackling in IT represents the greatest risk to the organization. To put it simply, don't patch = get hacked.
Cost
Reduce the number of unplanned IT operating expenses. Reduce the amount of staff at your helpdesk. Reduce your cost from reimaging computers due to malware / breach. Reduce the cost of fines and penalties caused by a compromised system.Risk
Reduce the risk of your data being held hostage by cyber criminals. Reduce the risk of your reputation being impacted due to breached system. Reduce the risk of customer data ending up in the wrong hands.Productivity
Allow your employees to focus on your business. Remove the "noise" from IT support allowing focus on transformation and customer service.-
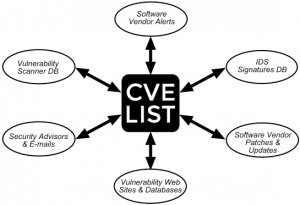
The Common Vulnerabilities and Exposures (CVE) database demonstrates the sheer volume of vulnerabilities that are reported daily and patched by vendors.
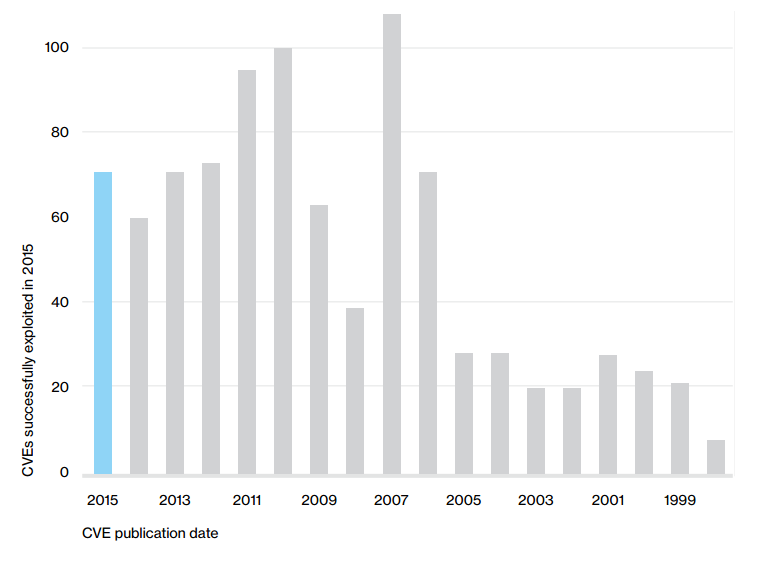
Responsible enterprises — and malicious adversaries — act on this information. Malicious actors race to develop working exploits by analyzing and reverse engineering each software patch. Delaying or ignoring patches for vulnerabilities considerably increases the chance of systems being exploited, in particular Internet connected systems. Recent research has found that for 88% of publicly disclosed vulnerabilities, a working exploit is available on the same day, which makes it imperative that patches be deployed immediately.
Industries which have regulation of protected data that we have a compelling solution to aid in compliance: